Expert Article: 12 Steps to successful Information Security Management
Security specialists Carsten Marmulla and Simon Decker are introducing the 12 steps to sustainable cyber security management.


Carsten Marmulla and Simon Decker from carmasec GmbH & Co. KG offer a new approach for SMEs that are facing the uphill battle of getting their company ready for ISM certification.

Allocating and controlling the tasks and responsibilities for information security and data protection in small and medium-sized organizations can be a major challenge for corporate management. New IT risks and vulnerabilities become known each and every day, and digitalization efforts are also increasing in pace, so that the task is not getting any easier.
There is basically no lack of available information and methods on these topics. However, most process documentation and methodological models are complex and usually designed for use in larger companies or organizations. As a result, smaller companies often feel neglected. The complexity and sheer quantity of the possible threats and the necessary measures often seem to be greater than the resources available for managing them. External support from consultants and experts regularly exceeds existing and planned budgets. It is also increasingly difficult to get specialized and skilled employees when you need them. Changes on the market as well as in regulations increase the requirements for professional risk management. Methodologies and frameworks can help to reduce this gap.
At the same time, the requirements for professional risk management in companies are increasing. On the one hand, this is due to market developments, and on the other hand, to the legislature. One example is the General Data Protection Regulation (GDPR), which has made a European export success of the protection of personal data, including a drastic increase in possible fines.
Even companies whose business model depends less on information technology, and which have a supposedly lower risk profile, will face a massive need for the expansion of their IT skills, due to the trend towards digitalization. This can be result either from their own initiative or from the pressure under which they are placed from competitors, customers or suppliers. For example, companies in the automotive sector have to be audited and certified based on their customers‘ purchasing requirements according to TISAX (an industry-specific variant of a management system for information security based on ISO 27001).
Small and medium-sized enterprises (SMEs), in particular, have to use their resources wisely. Often, however, medium-sized companies are economically unable to wait for the lengthy implementation of a management system. It can take anywhere from months to years from the initial decision and the first step of implementation to a successful certification audit, as processes, responsibilities, procedures, and company values need to be documented in a suitable way. This does not necessarily match the desired speed for the digital transformation of business processes – or of the whole company.
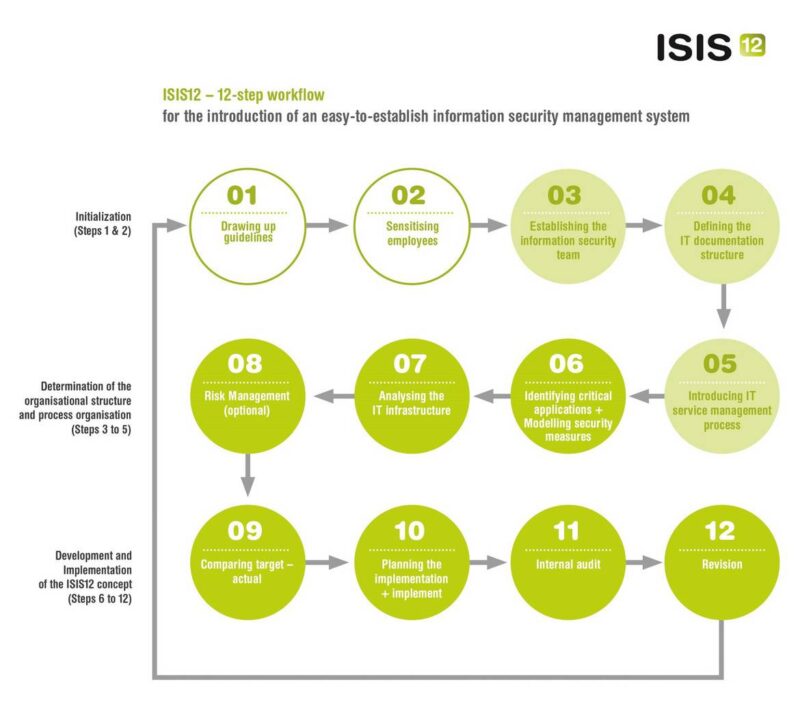 As a practical alternative to established large-scale and internationally approved standards for implementations of management systems for information systems – like ISO/IEC 27001 or the German baseline security standard (BSI IT-Grundschutz) – the IT-Security Cluster has designed an alternative especially focused on small and medium sized enterprises and organizations (SMEs/SMOs), called “Information Security in 12 Steps” (ISIS12).
As a practical alternative to established large-scale and internationally approved standards for implementations of management systems for information systems – like ISO/IEC 27001 or the German baseline security standard (BSI IT-Grundschutz) – the IT-Security Cluster has designed an alternative especially focused on small and medium sized enterprises and organizations (SMEs/SMOs), called “Information Security in 12 Steps” (ISIS12).
The IT-Security Cluster has designed an alternative especially focused on SMEs/SMOs, called “Information Security in 12 Steps” (ISIS12).
The process model itself is divided into 12 consecutive steps and three phases. This gives the user professional orientation as to which tasks still need to be completed.
The first phase consists of (1) developing an information security policy and (2) raising employee awareness for information security.
The second phase includes (3) the establishment of an information security team, (4) the definition of the IT documentation structure, and (5) the introduction of IT service management processes.
Based on this, the actual implementation starts in phase three. The existing IT structure has to be (6) analyzed and (7) business critical applications have to be identified. An (8) actual/target comparison is carried out and (9) appropriate security measures are designed. Appropriate (10) measures are planned, (11) implemented, and finally (12) reviewed. The Deming cycle (plan-do-check-act; PDCA) will be repeated on a regular basis, which leads to continuous improvement of the information security management system.
The procedural model requires far less effort to implement and can often be ready for certification in just a few months. However, even with this model, the existing documentation status is an essential aspect for the speed of implementation. As a result, the management of the company making the application in particular receives a methodologically mature process model, containing controllable measures and orientation to implement regulatory requirements for information security. Thanks to its compatibility with the international ISO 27001 standard, the existing management system can also be migrated at any time.

Carsten Marmulla is an experienced management advisor and technical consultant in the field of Information Security Management, GRC (Governance, Risk, Compliance), Data Protection, and IT Security.
He is certified as an internal auditor for the international standard for Information Security Management ISO/IEC 27001 and in accordance with the standards certified in ITIL v3, COBIT 4.1 and PRINCE2.

Simon Decker has specialist knowledge in the field of IT Security, network technology, and software development. A quick grasp of technical issues enables him to familiarize hiself with a wide variety of areas of technical spectrum.